Introduction
The nature of our digital communications today is such that you rarely communicate directly with your peers. It may seem that you and your friends are exchanging messages privately when, in reality, they're being recorded and stored in a central server.
You might not want your messages read by the server that's responsible for passing them between you and the receiver. In that case, end-to-end encryption (or more simply, E2EE) may be the solution for you.
End-to-end encryption is a method for encrypting communications between receiver and sender such that they’re the only parties that can decrypt the data. Its origins could be traced back to the 1990s, when Phil Zimmerman released Pretty Good Privacy (better known as PGP).
Before we get into why you might want to use E2EE and how it works, let’s look at how unencrypted messages work.
How Do Unencrypted Messages Work?
Let's talk about how a regular smartphone messaging platform might operate. You install the application and create an account, which allows you to communicate with others that have done the same. You write a message and enter your friend's username, then post it to a central server. The server sees that you've addressed the message to your friend, so it passes it along to the destination.

Users A and B communicating. They must pass data through the server (S) to reach each other.
You might know this as a client-server model. The client (your phone) isn't doing much – instead, the server takes care of all the heavy lifting. But that also means that the service provider acts as a middleman between you and the receiver.
Most of the time, the data between A <> S and S <> B in the diagram is encrypted. An example of this is Transport Layer Security (TLS), which is used extensively to secure connections between clients and servers.
TLS and similar security solutions prevent anyone from intercepting the message when it's moving from client to server. While these measures may prevent outsiders from accessing the data, the server can still read it. This is where encryption comes in. If data from A has been encrypted with a cryptographic key belonging to B, the server is unable to read or access it.
Without E2EE methods, the server can store the information in a database alongside millions of others. As large-scale data breaches have proven time and time again, this can have disastrous implications for end-users.
How Does End-To-End Encryption Work?
End-to-end encryption ensures that nobody – not even the server that connects you with others – can access your communications. The communications in question could be anything from plain text and emails to files and video calls.
Data is encrypted in applications like Whatsapp, Signal, or Google Duo (supposedly) so that only senders and intended recipients can decrypt them. In end-to-end encryption schemes, you might kick that process off with something called a key exchange.
What's a Diffie-Hellman key exchange?
The idea of the Diffie-Hellman key exchange was conceived by cryptographers Whitfield Diffie, Martin Hellman, and Ralph Merkle. It's a powerful technique that allows parties to generate a shared secret in a potentially hostile environment.
In other words, the creation of the key can occur on insecure forums (even with onlookers watching) without compromising the ensuing messages. In the Information Age, this is particularly valuable as parties don't need to physically swap keys to communicate.
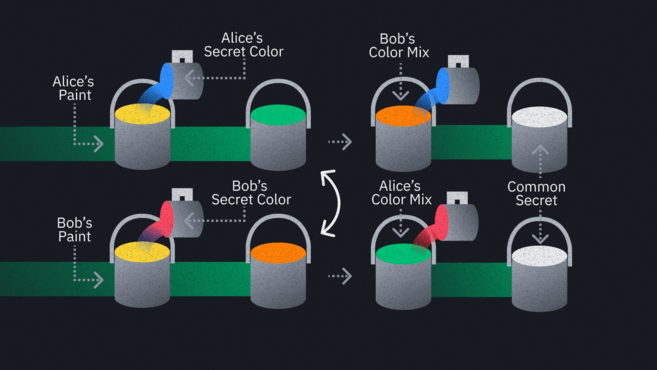
The exchange itself involves big numbers and cryptographic magic. We won't get into the finer details. Instead, we'll use the popular analogy of paint colors. Suppose that Alice and Bob are in separate hotel rooms at opposite ends of a hallway, and they want to share a particular color of paint. They don't want anyone else to find out what it is.
Unfortunately, the floor is swarming with spies. Assume that Alice and Bob can't enter each other's rooms in this example, so they can only interact in the hallway. What they might do is agree on a common paint in the hallway – say, yellow. They get a tin of this yellow paint, divide it between themselves, and return to their respective rooms.
In their rooms, they'll mix in a secret paint – one that no one knows about. Alice uses a shade of blue, and Bob uses a shade of red. Crucially, the spies can't see these secret colors they're using. They will see the resulting mixtures, though, because Alice and Bob now exit their rooms with their blue-yellow and red-yellow concoctions.
They swap these mixtures out in the open. It doesn't matter if the spies see them now, because they won't be able to determine the precise shade of the colors added in. Remember that this is only an analogy – the real mathematics underpinning this system makes it even harder to guess the secret “color.”
Alice takes Bob's mix, Bob takes Alice's, and they return to their rooms again. Now, they blend their secret colors back in.
Alice combines her secret shade of blue with Bob's red-yellow mix, giving a red-yellow-blue mix
Bob combines his secret shades of red with Alice's blue-yellow mix, giving a blue-yellow-red mix
Both combinations have the same colors in them, so they should look identical. Alice and Bob have successfully created a unique color that adversaries are unaware of.
So, this is the principle we can use to create a shared secret in the open. The difference is that we're not dealing with hallways and paint, but insecure channels, public keys, and private keys.
Exchanging messages
Once the parties have their shared secret, they can use it as the basis for an symmetric encryption scheme. Popular implementations typically incorporate additional techniques for more robust security, but all of this is abstracted away from the user. Once you connect with a friend on an E2EE application, encryption and decryption can only occur on your devices (barring any major software vulnerabilities).
It doesn't matter whether you're a hacker, the service provider, or even law enforcement. If the service is truly end-to-end encrypted, any message you intercept will look like garbled nonsense.
The Pros and Cons of End-To-End Encryption
Cons of end-to-end encryption
There's really only one downside to end-to-end encryption – and whether it's even a downside depends entirely on your perspective. To some, the very value proposition of E2EE is problematic, precisely because no one can access your messages without the corresponding key.
Opponents argue that criminals can use E2EE, safe in the knowledge that governments and tech companies can't decrypt their communications. They believe that law-abiding individuals should not need to keep their messages and phone calls secret. This is a sentiment echoed by many politicians who support legislation that would backdoor systems to allow them access to communications. Of course, this would defeat the purpose of end-to-end encryption.
It's worth noting that applications that use E2EE are not 100% secure. Messages are obfuscated when relayed from one device to another, but they're visible on the endpoints – i.e., the laptops or smartphones at each end. This is not a drawback of end-to-end encryption, per se, but it’s worth keeping in mind.

The message is visible in plaintext before and after decryption.
E2EE guarantees that nobody can read your data while it's in transit. But other threats still exist:
Your device could be stolen: if you don't have a PIN code or if the attacker bypasses it, they can gain access to your messages.
Your device could be compromised: your machine could have malware that spies on the information before and after you send it.
Another risk is that someone could insert themselves between you and your peer by mounting a man-in-the-middle attack. This would occur at the beginning of the communication – if you're performing a key exchange, you don't know for certain that it's with your friend. You could unknowingly establish a secret with an attacker. The attacker then receives your messages and has the key to decrypt them. They could trick your friend in the same manner, meaning that they could relay messages and read or modify them as they see fit.
To get around this, many apps integrate some kind of security code feature. This is a string of numbers or a QR code that you can share with your contacts via a secure channel (ideally offline). If the numbers match, then you can be sure that a third party isn't snooping on your communications.
Pros of end-to-end encryption
In a setup without any of the previously-mentioned vulnerabilities, E2EE is indisputably a highly valuable resource for increased confidentiality and security. Like onion routing, it's a technology evangelized by privacy activists worldwide. It's also easily incorporated into applications that resemble the ones we're used to, meaning the tech is accessible to anyone capable of using a mobile phone.
To view E2EE as a mechanism useful only for criminals and whistleblowers would be a mistake. Even the most seemingly secure companies have proven to be susceptible to cyberattacks, exposing unencrypted user information to malicious parties. Access to user data like sensitive communications or identity documents can have catastrophic impacts on individuals' lives.
If a company whose users rely on E2EE is breached, hackers can't extract any meaningful information about the content of messages (provided their encryption implementation is robust). At best, they might get ahold of metadata. This is still concerning from a privacy standpoint, but it's an improvement on access to the encrypted message.
Closing Thoughts
In addition to the applications mentioned earlier, there are a growing number of freely-available E2EE tools. Apple's iMessage and Google's Duo come bundled with iOS and Android operating systems, and more privacy- and security-conscious software continues to roll out.
Let's reiterate that end-to-end encryption isn't a magical barrier against all forms of cyberattack. With relatively little effort, however, you can actively use it to massively reduce the risk you expose yourself to online.
Disclaimer and Risk Warning: This content is presented to you on an “as is” basis for general information and educational purposes only, without representation or warranty of any kind. It should not be construed as financial, legal or other professional advice, nor is it intended to recommend the purchase of any specific product or service. You should seek your own advice from appropriate professional advisors. Where the article is contributed by a third party contributor, please note that those views expressed belong to the third party contributor, and do not necessarily reflect those of Binance Academy. Please read our full disclaimer here for further details. Digital asset prices can be volatile. The value of your investment may go down or up and you may not get back the amount invested. You are solely responsible for your investment decisions and Binance Academy is not liable for any losses you may incur. This material should not be construed as financial, legal or other professional advice. For more information, see our Terms of Use and Risk Warning.
