Introduction
It’s often considered critical to the functioning of a blockchain that the system is transparent. This means that every node on the network can store a copy and verify that no rules are being broken. For many distributed ledgers, anyone can load up an online block explorer that allows them to search through blocks, transactions, and addresses.
On the privacy front, this isn’t ideal. In a system like Bitcoin, every transaction can be linked back to a previous one. Coins are not technically fungible, meaning that each can be tied to specific transactions. No one can prevent you from sending bitcoin, but they can refuse to accept your transaction if those coins have previously passed through a blacklisted address.
In a worst-case scenario, a lack of fungibility could profoundly impact the very foundations of the system. Clean coins may fetch a premium, while older ones would be less valuable given their history.
Privacy in Bitcoin is often overstated. Not only can coins be traced, but users can, too. They enjoy pseudonymity (public addresses are visible instead of names), but this is not without its flaws. Sophisticated analysis techniques can, with increasing accuracy, cluster addresses together in an attempt to deanonymize network entities.
One upgrade proposed to make transactions truly private is Confidential Transactions.
What are Confidential Transactions?
Confidential Transactions (CT) were first discussed by Blockstream CEO Adam Back in 2013 and were later expanded upon by Bitcoin developer Gregory Maxwell. Maxwell outlined the problems mentioned in the first section (fungibility and weak pseudonymity) – and proposed a solution. Amounts transferred could be shielded from the broader network so that only the transacting parties would know how much had been sent.

Under normal circumstances (with publicly-viewable transactions), it’s easy for a node to verify that the amount received doesn’t exceed the amount sent. If Alice wants to send 0.3 BTC to Bob, she takes an unspent output (let’s call it 1 BTC) and breaks it into two pieces: 0.3 to be sent to Bob, and 0.69 to be sent back to her (with the rest forfeited as a mining fee).
This is simple algebra for other nodes: 1 exceeds 0.3 + 0.69, the signatures are all correct, and Alice’s inputs have not already been spent elsewhere, so the transaction must be valid. When amounts are blinded, however, things aren’t so trivial. How do you even begin to evaluate if an unknown amount equals or exceeds the sum of two other unknown amounts?
An overview of the cryptography involved
To hide data, encryption is required. However, traditional methods are akin to putting documents in a safe: once locked inside, it becomes unusable until it’s removed. What we need for Confidential Transactions to work is a digital safe whose contents are not revealed, but whose properties can be verified by an outsider.
The answer lies in homomorphic encryption specifically, in a scheme called a Pedersen commitment. This type of encryption allows an outsider to perform operations on encrypted data (which they can’t see) for a number of purposes.
A regular hash can be used to commit to data that you want to reveal later. Suppose that you want to announce a competition on social media, where whoever guesses your favorite exchange will win a prize of 0.01 BTC. Participants might be skeptical because you could just look at the answers after the competition’s close, and pick an exchange that hasn’t been mentioned.
What you could do is provide your followers with a hash: a string of seemingly random numbers and characters that maps to a specific input. You pass your exchange through a function in order to get a certain output. We’ll illustrate with the SHA256 algorithm:
f1624fcc63b615ac0e95daf9ab78434ec2e8ffe402144dc631b055f711225191Looking at this, you have no idea what the input was. Nor can you reverse the function to get it. If you know that the input was “Binance”, however, you can easily check that its hash matches the one listed above. In this way, your followers have some assurance that you will not change your answer at the close of the competition – doing so would produce a totally different output.
Realistically, though, this isn’t very secure. While your followers cannot reverse-engineer the algorithm, they can build a list of possible exchanges, hashing every single one until they get a match. We can reduce the likelihood of this by adding some random data called a blinding factor to the data we’re going to hash.
If we input “Binance is my favorite exchange I love it more than any other exchange 2#43Wr”, it becomes significantly harder for an opponent to guess (and for 0.01 BTC, it’s certainly unlikely that anyone would even attempt it).
A Pedersen commitment allows us to add the inputs behind the commitments. As Maxwell illustrates:
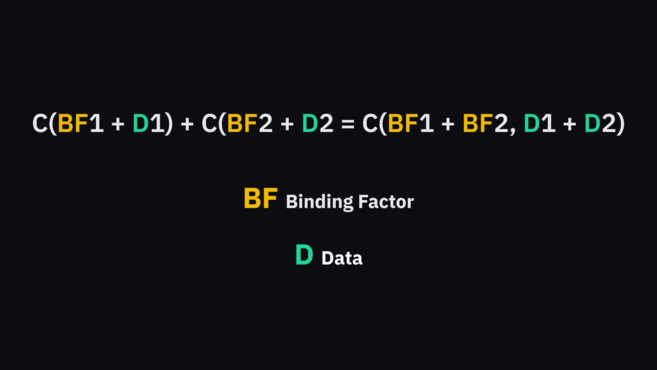
C(BF1 + D1) + C(BF2 + D2) = C(BF1 + BF2, D1 + D2)
Where BF is the blinding factor and D is the data
There are a few more steps from here involving elliptic curve cryptography and range proofs, but the basic idea is that a user has a Pedersen commitment for their address. When sending funds, two additional commitments are created (one for the change address to be returned to the user, and one for the destination address).
No one knows how much is being sent, but they can check that the change and destination commitments (the left side of Maxwell’s equation) add up to the originating address (the right side of the equation). If this evaluates correctly, then the user’s transaction is valid, as it can be proved that the inputs are equal to the outputs.
What can Confidential Transactions accomplish?
If Confidential Transactions were to be implemented in Bitcoin, we would enjoy a vastly more private system. Both inputs and outputs would be masked from the wider network, and entries on the ledger would be obfuscated - but nodes could still verify their authenticity.With this massive privacy boost, bitcoins may effectively be rendered fungible, as chain analysis no longer reveals the history of a given unit.
As to whether Confidential Transactions will be integrated into the protocol, it doesn’t seem likely at the current time. With this added functionality, transactions are much larger than standard ones – given limited blockspace, this would only increase demand. It would also require the majority of participants to agree to change the code, a task which has traditionally proved to be difficult.
Closing thoughts
Confidential Transactions have seen some iterations in other cryptocurrencies and Bitcoin sidechains. For instance, Monero uses them in combination with constructs called ring signatures to achieve anonymity and fungibility. The Liquid sidechain implements them for greater privacy, and MimbleWimble extends them to the same ends.
For the benefits they bring, Confidential Transactions come with the trade-off of a bigger footprint. Cryptocurrencies often struggle with scalability and throughput at the base layer, and larger transaction sizes do not appeal to all. That said, privacy advocates believe it essential to hide transaction amounts and participants to truly allow cryptocurrency to serve as fungible money.
